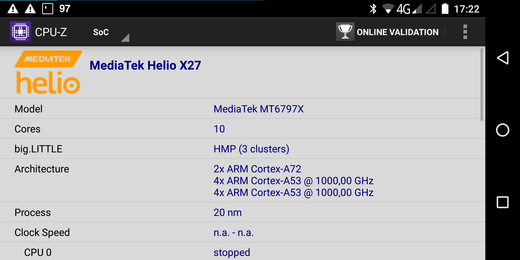
Improved modular Linux kernel for the Gemini PDA
The linux kernel binary I have shared in the article Modular Linux kernel for the Gemini PDA turned out to lack some important features, like not supporting the ethernet port of the Planet Computers USB hub. Thus a second version of the kernel had to be built.
In addition to the original changes, the following changes to the kernel configuration have been performed:
•Enabled modules for more USB devices
•Disabled CONFIG_MTK_CPU_HOTPLUG_DEBUG_0 (for less pollution in dmesg)
•Disabled CONFIG_MTK_CPU_HOTPLUG_DEBUG_3 (for less pollution in dmesg)
•Enabled CONFIG_RCU_FAST_NO_HZ (for improved energy efficiency)
•Enabled CONFIG_RCU_BOOST (for better performance)
Originally I intended to also disable CONFIG_MTK_CPU_HOTPLUG_DEBUG_2, but then the build fails with an error regarding a static struct declaration.
The changes result in this kernel configuration: gemini-3.18.41+-config.gz (13990 downloads )
For the build, the updated kernel source the from https://github.com/gemian/gemini-linux-kernel-3.18 with the fix for the Bluetooth vulnerability cve-2017-1000251 has been used.
Again the kernel modules for the iptables MIRROR target (will not be usable with the default iptables version on the Gemini) and frandom have been added.
Those who do not want to go through the build themselves can download my prebuild kernel from here:
Kernel Image: linux_boot-gemini-3.18.41+.img (464 downloads )
Modules: modules_firmware-gemini-3.18.41+.tar.gz (17121 downloads )
Downloads outdated, new version at: Another improved modular Linux kernel for the Gemini PDA
Instructions for flashing the image can be found on: support.planetcom.co.uk. Make sure to use the same scatter file that has been used for the initial flashing. Using the Download only mode of the flash tool is sufficient. Uncheck all partitions but linux_boot (or boot if you boot into linux as default). For the linux_boot respectively the boot partition select the downloaded kernel image. With newer scatter files the boot partition names have changed to boot, boot1 and boot2. Select the appropiate one for your Gemini.
Alternatively you can flash the kernel using dd:
dd if=linux_boot-gemini-3.18.41+.img of=/dev/block/disk/by-partlabel/boot
If Linux is not your primary operating system on the Gemini use boot1 or boot2 instead, depending on your partition layout.
After flashing, copy the modules archive onto your Gemini and extract it in your root directory:
cd /
tar -xzf /path_to/modules_firmware-gemini-3.18.41+.tar.gz
After rebooting the device some more USB peripherals, including the ethernet port of the Planet Computers hub, should work.
Regards
Jürgen
 MyGNU.de
MyGNU.de












![Validate my RSS feed [Valid RSS]](https://validator.w3.org/feed/images/valid-rss.png)

